What Is The Dark Web?

The Dark Web, a mysterious and often misunderstood corner of the internet, exists as a realm where anonymity and privacy are paramount. Unlike the surface web that most users are familiar with, where information is indexed and accessible through standard search engines like Google, the Dark Web operates on encrypted networks that obscure user identities and activities.
What is the Dark Web?
The Dark Web refers to a part of the internet that is not indexed by traditional search engines like Google, Bing, or Yahoo. Unlike the surface web, which is accessible to anyone using standard browsers, the Dark Web requires specific software, configurations, or authorization to access. It exists on overlay networks that use non-standard communication protocols and encryption to ensure anonymity and privacy for its users.
Characteristics of the Dark Web
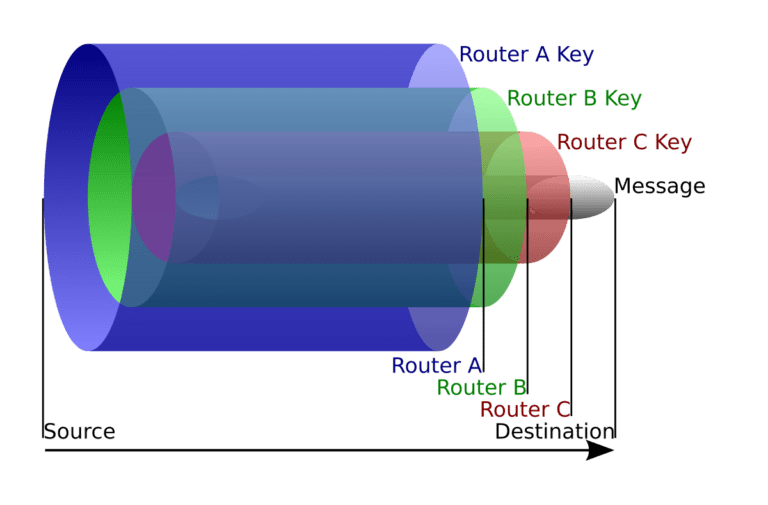
Anonymity and Privacy: One of the defining features of the Dark Web is its emphasis on anonymity. Users often access it through networks like Tor (The Onion Router), which routes internet traffic through a series of volunteer-operated servers to conceal a user’s location and usage from surveillance or traffic analysis.
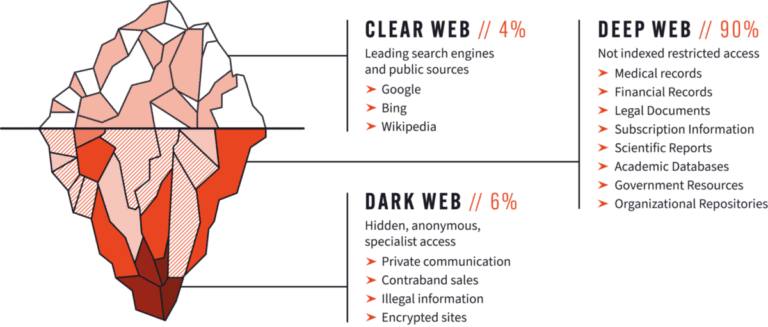
Non-Indexability: Websites on the Dark Web do not have traditional domain names like .com or .org. Instead, they use .onion domains, which are only accessible through Tor or similar anonymizing networks. This lack of indexing makes it challenging for users to find specific sites without prior knowledge or specialized directories.
Unregulated Content: Due to its anonymity and lack of oversight, the Dark Web hosts a wide range of content, including both legal and illegal activities. This includes forums, marketplaces, chat rooms, and sites dedicated to privacy, activism, journalism, and more controversially, illicit trade in drugs, firearms, stolen data, and other illegal goods and services.
How Does the Dark Web Operate?
Accessing the Dark Web typically involves downloading and configuring software like the Tor Browser, which is designed to anonymize internet traffic and provide access to .onion websites. Other networks and tools, such as I2P (Invisible Internet Project) and Freenet, offer similar capabilities, each with its own set of protocols and user base.
The anonymity provided by these networks relies on layered encryption and routing methods that obfuscate the origin and destination of data packets. This makes it difficult, though not impossible, for authorities to trace users engaging in illegal activities or for websites to be taken down by traditional means.
Uses of the Dark Web
Despite its association with illicit activities, the Dark Web serves various legitimate purposes:
Privacy Advocacy: Some users access the Dark Web to communicate anonymously, particularly in regions with restricted internet access or where freedom of speech is curtailed.
Whistleblowing and Journalism: Journalists and whistleblowers use the Dark Web to publish sensitive information securely, away from government censorship or corporate influence.
Research and Education: Security researchers, academics, and cybersecurity professionals explore the Dark Web to study cybercrime trends, vulnerabilities, and the evolution of digital threats.
Cryptocurrency and Finance: The Dark Web has been an early adopter of cryptocurrencies like Bitcoin due to their pseudonymous nature, enabling secure transactions outside of traditional banking systems.
Concerns and Ethical Considerations
Despite its potential benefits, the Dark Web raises significant ethical and security concerns:
Illegal Activities: The Dark Web facilitates a substantial amount of illegal trade, including drugs, weapons, counterfeit currency, and stolen data. Law enforcement agencies face challenges in combating these activities due to the anonymity provided by the network.
Exploitation and Harm: Activities such as human trafficking, child exploitation, and cyber extortion thrive in the shadows of the Dark Web, exploiting vulnerable individuals and perpetuating societal harm.
Privacy vs. Security: The balance between individual privacy rights and the need for law enforcement to investigate and prevent criminal activities is a contentious issue, often debated in legal and ethical circles.
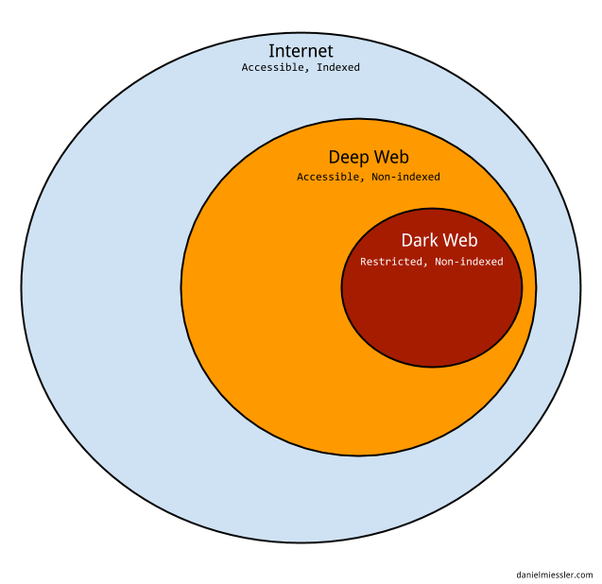
Difference Between Surface Web and Dark Web
The terms “Surface Web” and “Dark Web” refer to different segments of the internet, each with its own characteristics, accessibility, and purpose.
Surface Web: The Surface Web is the portion of the internet that is accessible to the general public through standard search engines like Google, Bing, or Yahoo. It includes websites and content that are indexed and readily available without special tools or permissions. Common examples include news websites, social media platforms, online shopping sites, and informational resources. The Surface Web is characterized by its visibility and accessibility, meaning that anyone with an internet connection and a web browser can easily navigate and interact with these sites. It represents the majority of the web in terms of content volume and user activity.
Dark Web: The Dark Web is a hidden part of the internet that is not indexed by traditional search engines and requires special software to access, such as Tor (The Onion Router). Unlike the Surface Web, the Dark Web operates on encrypted networks and is designed to provide anonymity to both users and website operators. It is often associated with activities that seek to preserve privacy or engage in illicit activities, such as illegal marketplaces, forums, and other sites that deal in stolen data or contraband. While the Dark Web is sometimes linked to criminal behavior, it also serves legitimate purposes, such as providing a platform for whistleblowers, journalists, and individuals living under oppressive regimes to communicate and share information securely.
Step-by-Step Guide to Accessing the Dark Web Legally
1. Understand the Legal Implications
Before proceeding, it’s crucial to understand the legal risks and implications of accessing the Dark Web. While using anonymizing software itself is legal in most countries, engaging in illegal activities on the Dark Web (such as purchasing illegal goods or services) is illegal and can lead to severe consequences.
2. Download and Install Anonymizing Software
The most common way to access the Dark Web is through the Tor (The Onion Router) network. Tor is free and open-source software that enables anonymous communication by directing internet traffic through a worldwide volunteer network of servers.
-
Download Tor Browser: Go to the official Tor Project website (https://www.torproject.org/) and download the Tor Browser for your operating system (Windows, macOS, Linux).
-
Install Tor Browser: Follow the installation instructions provided on the Tor Project website. The Tor Browser is pre-configured to protect your anonymity and allows you to access .onion websites (the domain suffix used by Dark Web sites).
3. Configure Tor Browser
Configuring Tor Browser is crucial for ensuring both privacy and security while browsing the internet anonymously.
To start, download and install Tor Browser from the official Tor Project website to avoid malicious versions. Once installed, launch the browser and follow the setup wizard, which will prompt you to connect to the Tor network.
During the initial configuration, you may need to select “Connect” or “Configure” based on your network environment and any specific privacy needs, such as using a proxy. After connecting, Tor Browser will automatically adjust its settings to route your traffic through the Tor network, providing anonymity by encrypting and bouncing your connection through multiple nodes globally.
To enhance security further, regularly update Tor Browser to the latest version to benefit from security patches and improvements. Additionally, avoid installing unnecessary add-ons or plugins, as they can compromise your anonymity. By carefully configuring and maintaining Tor Browser, you ensure a secure and private browsing experience.
4. Access Dark Web Sites
With Tor Browser installed and configured, you can now access .onion websites:
-
Visit Dark Web Directories: There are directories and search engines specifically for .onion sites that list various websites available on the Dark Web. Some examples include the Hidden Wiki (http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page) and Daniel’s Onion Link List (http://donionsixbjtiohce24abfgsffo2l4tk26qx464zylumgejukfq2vead.onion/).
-
Use Caution: Be cautious when exploring the Dark Web. While not all content on the Dark Web is illegal or malicious, there is a higher risk of encountering illegal activities, scams, and malware compared to the surface web. Exercise discretion and avoid engaging in any illegal activities.
5. Practice Safe Browsing Habits
To protect yourself while accessing the Dark Web:
-
Stay Anonymous: Avoid revealing personal information or using accounts that can be traced back to your identity.
-
Keep Software Updated: Ensure your Tor Browser and antivirus software are up to date to defend against potential security threats.
-
Understand Risks: Be aware of the risks associated with accessing the Dark Web and avoid engaging in activities that compromise your safety or legality.
6. Legal and Ethical Considerations
-
Observe Local Laws: Abide by local laws and regulations regarding internet usage and cybersecurity.
-
Avoid Illegal Activities: Refrain from participating in or supporting illegal activities, as this can have severe legal consequences.
By following these steps and exercising caution, you can access the Dark Web legally and responsibly while minimizing risks to your security and legal standing.
Navigating the Dark Web: A Step-by-Step Guide
1. Install and Configure Tor Browser
The Tor Browser is the most commonly used tool to access the Dark Web. It anonymizes your internet traffic by routing it through a series of encrypted nodes, making it difficult to trace your online activity. Follow these steps to get started:
-
Download Tor Browser: Go to the official Tor Project website (https://www.torproject.org/) and download the Tor Browser for your operating system (Windows, macOS, Linux).
-
Install Tor Browser: Once downloaded, follow the installation instructions provided on the website. Tor Browser is pre-configured to protect your anonymity and enable access to .onion websites (specialized domains used on the Dark Web).
2. Accessing .onion Websites
.onion websites are not indexed by traditional search engines and require specific URLs or directories to find:
-
Use Dark Web Directories: There are several directories and search engines tailored for the Dark Web that list .onion websites categorized by topic or purpose. Examples include:
-
The Hidden Wiki: A popular starting point for finding .onion links across various categories. Accessible through Tor at http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page.
-
Daniel’s Onion Link List: Another comprehensive directory listing .onion sites, accessible at http://donionsixbjtiohce24abfgsffo2l4tk26qx464zylumgejukfq2vead.onion/.
-
-
Bookmark Trusted Sites: Once you find a .onion site of interest, you can bookmark it within Tor Browser for easy access in the future.
3. Safe Browsing Practices
Navigating the Dark Web involves potential risks due to the presence of illegal activities, scams, and malware. Follow these practices to stay safe:
-
Avoid Suspicious Links: Only visit websites from trusted directories or sources. Be cautious of links shared in forums or on social media platforms, as they may lead to malicious sites.
-
Verify URLs: Double-check URLs before accessing them to ensure they lead to legitimate .onion sites and not phishing pages or scams.
-
Use Security Features: Tor Browser includes security features like NoScript (to prevent JavaScript execution) and HTTPS Everywhere (to force HTTPS connections) to enhance your browsing security.
4. Understanding .onion Addresses
.onion addresses are unique domain names used exclusively on the Tor network:
-
Format: .onion addresses are alphanumeric strings followed by “.onion” (e.g., http://example.onion/). They are randomly generated and provide a level of anonymity by hiding the server’s IP address.
-
Bookmarking: Due to their complexity and unmemorable nature, bookmark .onion addresses of interest within Tor Browser to revisit them easily.
Navigating the Dark Web requires a different approach compared to the surface web, emphasizing privacy, caution, and awareness of potential risks. By following these steps and practicing safe browsing habits, you can explore the Dark Web effectively while minimizing security threats and legal concerns. Always prioritize your safety and adhere to ethical guidelines when interacting within the Dark Web environment.





Post Comment